MineSweeper, with no luck – An Introductory blog to Reverse Engineering
Hello Folks, This blog articulates the start of my Reverse Engineering journey. As this is an introductory blog and a foundation step in my journey of Reverse Engineering, please bear with my mistakes. In this blog, I did reverse engineering of the MineSweeper Windows application and tried to find all the mines and complete the game. This is not the only method that can be used, but one of them, we will use other enhanced methodologies to perform the same in an efficient manner in the upcoming blogs of this series.
Table of Contents
ToggleLet us Reverse!
First things first, let’s start olly debugger, we will use Olly debugger only for the purpose of reverse engineering in this blog, and open minesweeper’s exe from the menu. Olly will open it’s CPU information(assembly program), or we can manually navigate to the menu bar, View > CPU. Currently, the application is not running, so the bottom right corner will display as paused. Let us navigate to its memory dump, In the menu, View > Memory.
What is Memory Dump?
A memory dump records all the contents of system memory when your computer stops unexpectedly. A memory dump may contain data from processes that were running when the memory dump was collected.
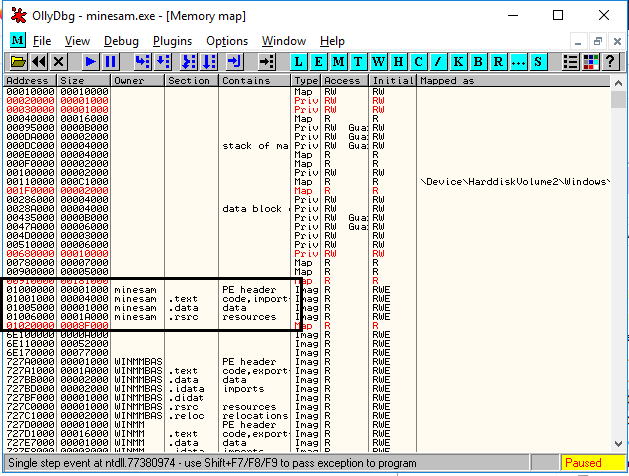
Search the application name in the owner column, now in the memory map window against the targetted application
we can find .text and .data.
- .text – Application code can be found here.
- .data – Application data is recorded based on the usage.
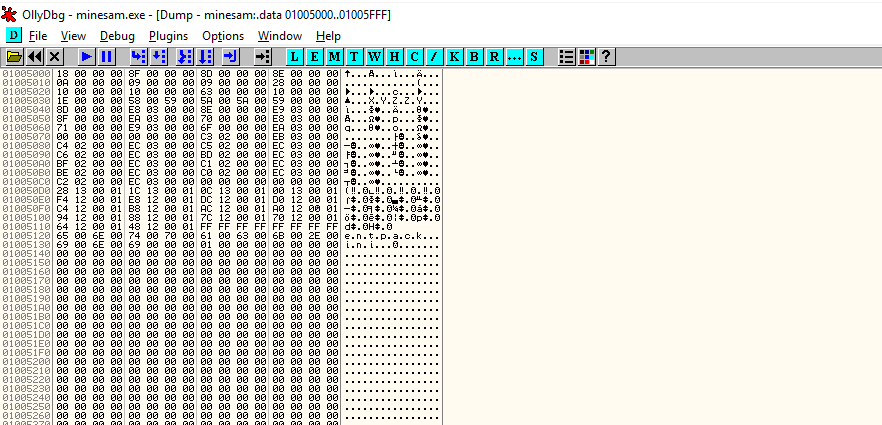
.data seems to be our target, right click on .data and dump. This will open the memory dump of the application, but the application is yet not attached to the debugger(It is still paused). Before attaching the application, let’s observe the dump file, only zeros can be seen. It is because the application is yet not attached.

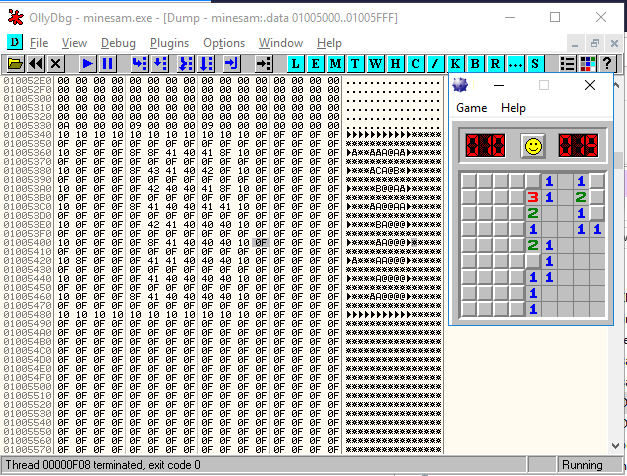
So, to start the application go to the top menu Debug > Run; this will move CPU information from 64 bit to 32 bit and repeat the process to attach the application. Now the application is being monitored by our debugger, time to find the difference in the dump file. Near the memory address 01005340, we can observe the change and a pattern too, seems like our game board.
It seems the game board lies in between memory address 01005340 and 01005480. To confirm, trying luck on the game board, observe change of hex value in our targetted memory address range.
- 42 represents number 2
- 41 represents number 1
- x8f represents a mine
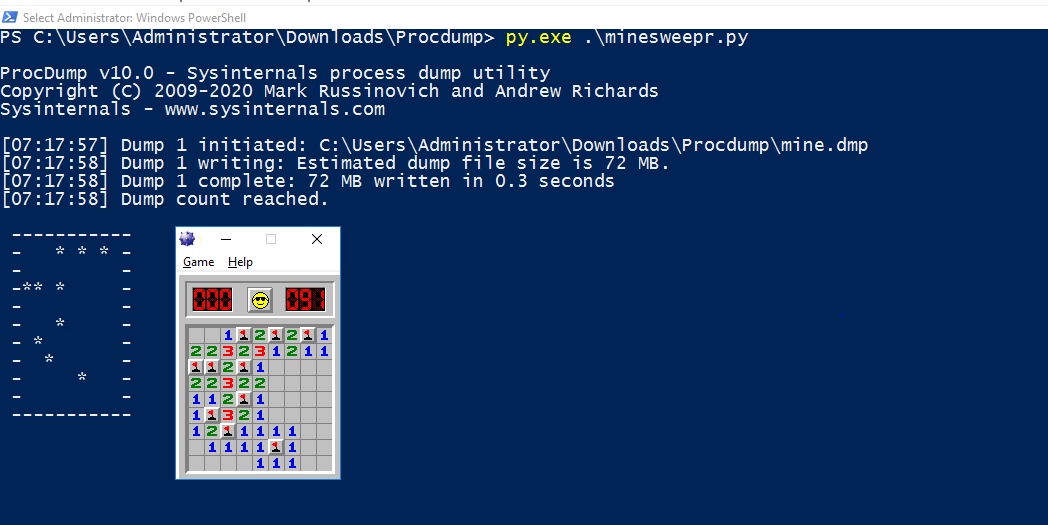
Now, we can cheat the game by manually identifying the memory address of mines but let us automate this process with the help of ProcDump and python.
What is ProcDump?
ProcDump is a command-line utility whose primary purpose is monitoring an application for CPU spikes and generating crash dumps during a spike that an administrator or developer can use to determine the cause of the spike.
Python to rescue:
import os
# Dump memory
cmd = "del mine.dmp"
os.system(cmd)
cmd = "procdump -ma minesam.exe mine" #Write a dump file with all process memory
os.system(cmd)
# Find gameboard
mark ='x10x10x10x10x10x10x10x10x10x10x10x0F'
line_length = 32
board_size = 500 # characters in whole board
with open("mines.dmp", "rb") as f:
data= f.read()
start = data.find(mark)
if start <0:
print "No Gameboard found"
for i in range(0, board_size, line_length):
line = ''
for j in range(line_length):
g = data[start+i+j]
if g == 'x10':
c = "-"
elif g == 'x0f':
c = " "
elif g == 'x8f':
c = "*"
elif g == 'x00':
c = " "
else:
c = chr( ord(g) - 16 )
line += c
print lineLet us run the script …
With this information, we can pick all the numbers with no luck.
Happy Hacking!
Suggested Read – Minesweeper Hacked : How We Hacked an Android Game And Ranked First globally
Resources
About Payatu
Payatu is a boutique security testing and services organization specialized in Products, Applications, and Infrastructure security assessments and deep technical security training. We offer a full IoT ecosystem security assessment, including Hardware, Cloud, Web, and Mobile interfaces.
Get in touch with us. Click on the get started button below.