Introduction
Welcome back! I hope you have gone through the previous blogs, where we discussed about can-utils. In this blog we will try to look into some of the prominent car hacks happened. we discussed about Automotive attack surface, CAN protocol, tools etc. In total we have an idea of Automotive security and different challenges as an industry we are facing. While discussing vehicle attack surface we saw a range of fields which can be vulnerable to attacks, because interface joints create more chances of getting a vehicle hacked. Today we will look into some popular scenarios where a car got pwned !
Table of Contents
ToggleFamous Jeep Hack
The history of car hacking incidents started back in 2015, when researchers chris and charlie were able to pwn a 2015 zeep cherokee remotely and they full control of steering, brakes, infotainment hub. Their research Is a culmination of three years into automotive security.
They successfully demonstrated a remote attack that can be performed against many Fiat-Chrysler vehicles. The number of vehicles that were vulnerable were in the hundreds of thousands and it forced a 1.4 million vehicle recall by FCA as well as changes to the Sprint carrier network.
This remote attack could be performed against vehicles located anywhere in the United States and requires no modifications to the vehicle or physical interaction by the attacker or driver. As a result of the remote attack, certain physical systems such as steering, and braking are affected.
While reversing the vehicle they found that Uconnect 8.4AN RA4 from Harman Kardon as the sole source for infotainment, Wi-Fi connectivity, navigation, apps, and cellular communications and it can communicate with internal CAN Bus and also it can receive instructions OTA.
But there is a theoretical air gap between them. When initially they ran Nmap scan on the vehicle they found an open port 6667/tcp which open and runs irc. In fact, it was D-Bus which is being used for inter- process communication. Jeep did not require any authentication.
The researchers used Dfeet tool to look at the services and Dbus-Python scripts for more. Dbus services were not made to talk to outside the vehicle environment, it was purely for intercommunication purposes.
Command line injection was then done by simply connecting to the vehicle WIFI. Later they the same was done via sprint network by simply changing the ip address in their 4-line python code. This time they did basic request to dump VIN number and GPS coordinates over the network to see how many vehicles are vulnerable. Their estimate was 400,000, but in reality, it was 1.4 million.
The airgap actually has a SPI line connecting the OMAP chip and V850, but in fact, it’s a 2-step process.
- Command Line Injection.
- Reprogramming the V850
The OMAP chip and V850 chip are not programmed to use the SPI line between them, unless you reprogram the V850’s SPI parser to collect bytes from SPI line, repack them as CAN packets, and inject the same on CAN bus.
The V850 chip doesn’t require any code validation to reflash a modified binary. You can do it from the infotainment hub also. So, all you would need now is the CAN packets to be sent.()
If we see the jeep case it’s a classic exploitation of interface joints and leveraging multiple potential vulnerable interfaces.
There were no firmware validations, no proper input filtering both at 6667 port and in the OMAP chip and the airgap is also not perfect. This might not be possible by simply using proper data validation.
Skyo-go research on Mercedes Benz
In 2019, a security research team Skyo-Go from China which focuses on connected cars security. They build a testbench and their initial attack vectors are Head unit, OBD-II port and Hardware for Enhanced Remote Mobility & Emergency Services (HERMES) of a Mercedes Benz car.
The head unit uses windows CE Automotive 7 which is not an open-source software. So, the no source code and debug environment will not be publicly available. And we all know that OBD-II port requires physical access thus demoting the severity to low.
HERMES designed by Harman Kardon contains a 4G module which connects the car to internet. It uses embedded Linux and it handles emergency calls, remote/local diagnosis which communicates with each ECU. It also provides 2.4GHz and 5GHz functions to the head unit. A user manual of HERMES is leaked online & is on a publicly available database, which has the pinout information.
The Head unit needs to connect to the TCU to access the Internet.
It has three ways to connect with TCU:
- USB UTC
- Bluetooth DUN
- The Wi-Fi.
The configuration file in the system determines the actual connection method. Before establishing a connection between HU and TCU, they need to negotiate protocols through CAN-A. After the connection is established, they manage the network through WCC protocol.
The Head unit connects to 2 CAN-buses:
- CAN-D, which is a comfortable can bus.
- CAN- HMI.
Mercedes Benz also has Anti-theft warning systems, but it can be bypassed by blocking some data at CAN bus level for capturing anti-theft Level – A deactivate message.
Further reversing the CAN bus packets they found that certain CAN Bus messages keep the Head unit running and two different heartbeat messages are needed to bypass the HU anti-theft system and make it run on the bench.
Firmware is one of the essential’s in attacking any embedded device. So, OpenOCD was used with FT2232 to dump the firmware. You have to disable the watchdog times as it might reset the device while reading the firmware.
Using the JTAG interface on the 4G module they triggered the break pointer which allows to read/write the memory. It’s a difficult path because you have to reverse engineer the kernel and find the register for NAND controller.
The other way they found to get the firmware is by opening the cellular module that has an eMCP NAND flash and uses a BGA work station to extract the firmware. They also made PCB adapters/circuits which workout all the 48 pin to support both 8 bit and 16 bits NAND flash.
In qualcomm modules the partitions start with special magic bytes. A python script which can parse the dump was made too. In fact, very deep and significant work was put into dumping and figuring out the partitions.
There was no secure boot, and the Skyo-go team was able to modify the system service to open a debug shell as well.
Stealthy Drone attack on Tesla model’s – S, 3, X & Y
In 2019 PWN2OWN, Tesla model 3 was a target in the automotive category, and the in-scope targets are Modem, WIFI/Bluetooth, Intainment hub, Gateway/Autopilot, Autopilot DoS and Key fob.
This caught the interest of security researchers Ralf-Philipp Weinmann and Benedikt Schmotzle and they started buying salvaged parts from the flea market with the focus of attacking VCSec and infotainment.
They were successful in finding a remote zero-click security vulnerabilities in an open-source software component (ConnMan) used in Tesla automobiles that allowed them to compromise parked cars and control their infotainment systems over Wi-Fi.
They exploited the functionality of Tesla Model 3 which automatically connects to Tesla Service WI-FI. By fusing two vulnerabilities in two components of ConnMan Deamon (Connman is default on Automotive grade Linux recommended by GENIVI), which allowed them to execute a remote code execution on the Infotainment system, a stack over flow in DNS forwarder and a stack info leak in the Dynamic Host Configuration Protocol (DHCP) component.
CVE-2021-27765 was used to gain control on ConnMan which is a connection management daemon for managing internet connections within the devices running in a Linux operating system.
This even allows them to shut down the firewall, change routing tables and load/unload kernel modules.
When a tesla vehicle is parked, it generally scans for Wi-Fi networks and tries to connect to the SSID “Tesla Service” which uses WPA2-PSK, but the credentials were found in the firmware.
Researcher’s used wpad to froward requests to local ConnMan DNS and DHCP stack info leak to determine the software version running along with “libc base and stack base”. And a reverse TCP connect fetches the 2nd stage payload. They used drones to deploy this attack for a stealthy mode of action.
In this case, the ConnMan bugs were there for almost 7 years forming the basis of a complete attack. This is a case in which an attacker/adversary can leverage exixting vulnerabilities to hack into the car/vehicle.
Simple bugs or security gaps can be joined to access/attack an entire fleet. in these cases, the damage The damage in such cases will be catastrophic.
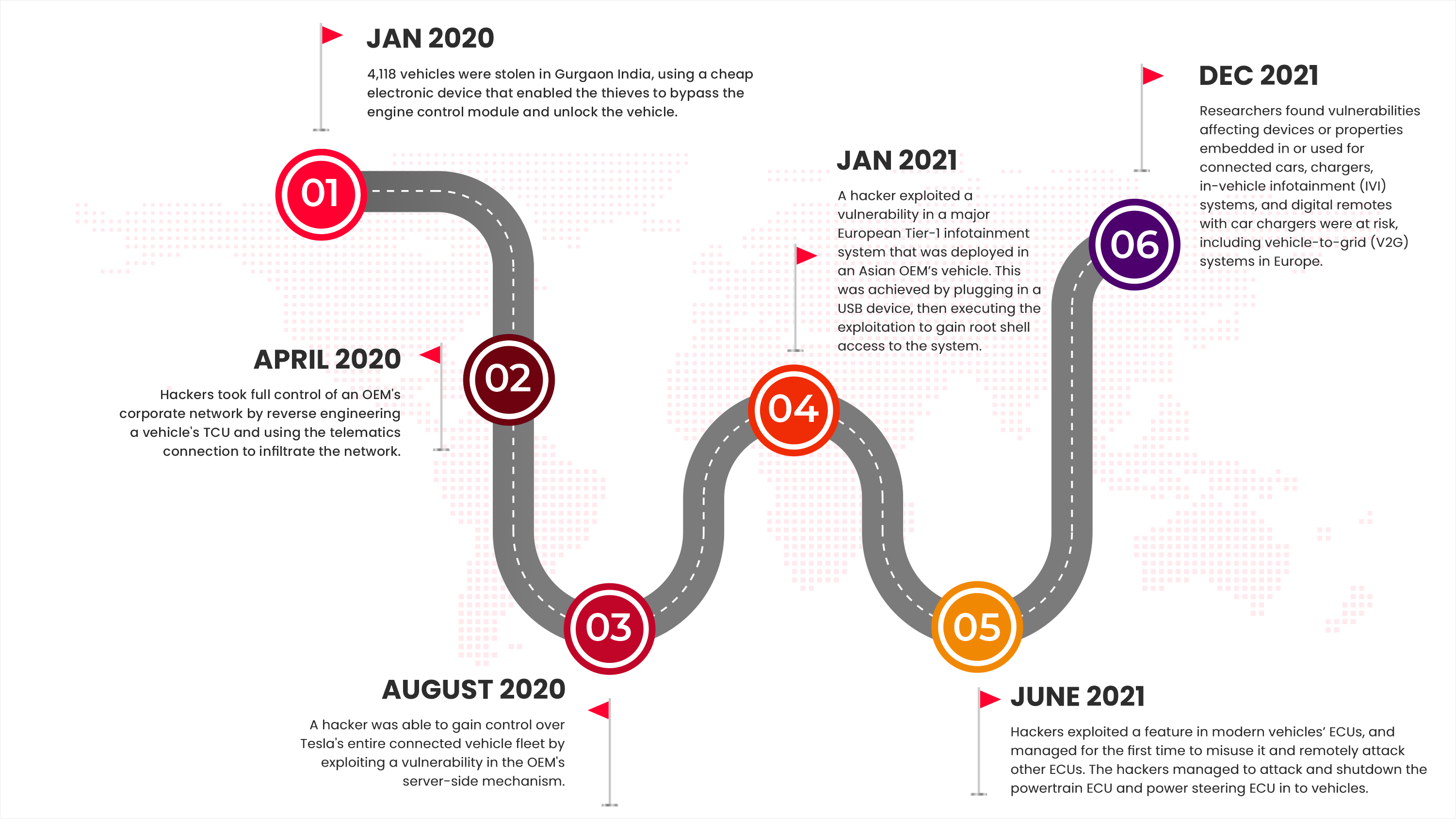
Below is some of the other attacks happened in vehicle ecosystem which are more spread far and wide.
Conclusion:
There are many different attacks related to Vehicles and their backend. In this blog, we picked up a few of them to show the various attack possibilities in the Automotive ecosystem, ranging from hardware, firmware, radio, etc. We hope you got the idea of the threat on the Automotive ecosystem and why it is so essential to gear up it’s security.
Refrences:
- Remote Exploitation of an Unaltered Passenger Vehicle
- DEF CON 23 – Charlie Miller & Chris Valasek – Remote Exploitation of an Unaltered Passenger Vehicle
- us-20-Yan-Security-Research-On-Mercedes-Benz-From-Hardware-To-Car-Control
- TBONE: for public release on 2021-04-28
- CANSECWEST 2021: Tbone Drone vs Tesla – Ralf-Philippe Weinmann & Benedikt Schmotzle, Comsecuris
About Payatu
Payatu is a research-powered cybersecurity service and training organization specialized in IoT, embedded, mobile, cloud, infrastructure security, and advanced security training. We offer a full IoT/IIoTT ecosystem security assessment, including hardware, firmware, middleware, and application interfaces. If you are looking for security testing services then let’s talk, share your requirements: https://payatu.com/#getstarted Payatu is at the front line of IoT security research, with a great team, and in house tools like expliot.io. In the last 8+ years, Payatu has performed, security assessment of 100+ IoT/IIoT product ecosystems and we understand the IoT ecosystem inside out. Get in touch with us. Click on the get started button below.


