Introduction
This is the first blog of the series to discuss security issues in the
automotive domain. With the connected car concept the bidirectional
vehicle to vehicle (V2V) communication has become a significant part in
autonomous vehicles. Thus security threats are not only limited to a
smart car but to autonomus cars as well.
Table of Contents
ToggleIn this blog basic attacks on automotive systems will be discussed.
Introduction to Automotive electronics subsystems
Today’s vehicles consist of electronic systems right from the headlight
of a car and LED brake light to the seat control inside the car. The
manufacturers have improved the performance of the vehicle by deploying
different embedded subsystems. The systems have become core of the
automotive architecture.To name a few following are the embedded
subsystems in a vehicle
1.Engine ignition
2.Fuel Injection
3.Anti lock brakes
4.Seat control
5.Infotainment system
6.Transmission control
7.Security alarms
8.Light controls
9.Windows control
The onboard devices of a car are controlled by Electronic Control Unit
(ECU). The heart of any electronic automotive system is an engine
control that critically responds in real time systems. The engine
control unit is a 32 bit microcontroller unit (MCU), it is responsible
for controlling the process of fuel injection,emission control,AC
systems etc.
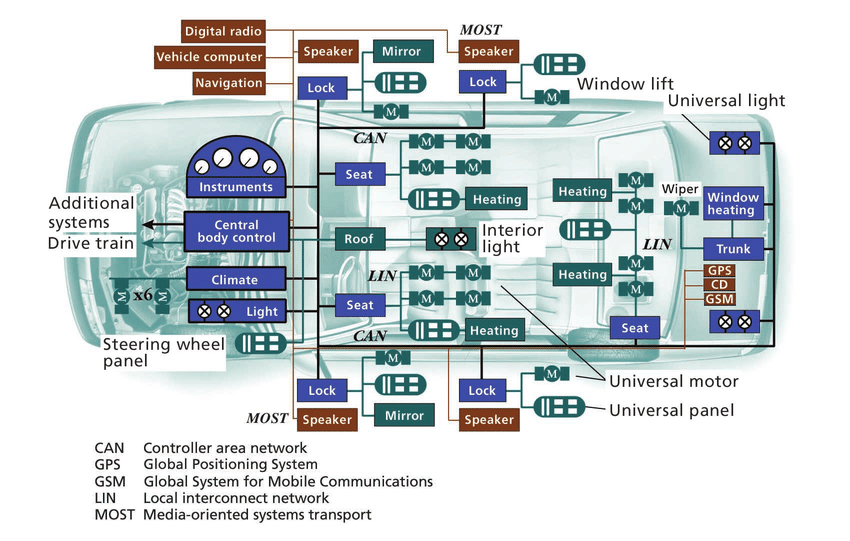
The figure below shows high level architecture of automotive vehicle
where different parts of vehicle mentioned above communicates with ECU.
Source : Leen, Gabriel & Heffernan, D.. (2002). Expanding automotive
electronic systems. Computer. 35. 88-93. 10.1109/2.976923.
Automotive Attack Methods
The growing embedded subsystems in an automotive and their internal
communication have created opportunities for attackers to execute
various attacks on them. Here we will begin discussing possible attacks
in the automotive scenario.
An attacker who wishes to take control of a vehicle finds out the
following ways to compromise an electronic control unit (ECU) and finds
the feature of an attack.
1.Physical attacks : This involves attacker to access physical ports
such as USB, OBD -II and sniff the data.
2.Wireless attacks : These involve attacks on short and long range
wireless communication viz. Wi-Fi, BLE, NB-IoT and GSM
3.Sensor attacks : The automotive sensors such as GPS, IMU,LIDAR,
RADAR,camera involves sensor fusion for autonomous systems and are major
threats to get manipulated.
When combined above attacks results in different attack surfaces. One
such attack surface on a high level is an automotive infotainment system
also called IVI (In Vehicle Infotainment) system . We will explore it in
detail further.
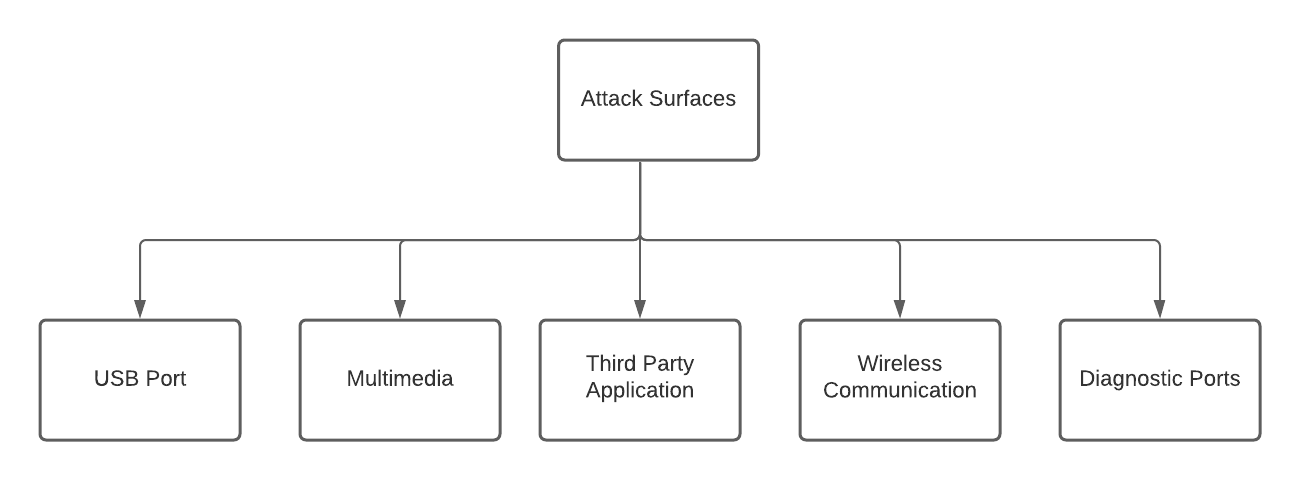
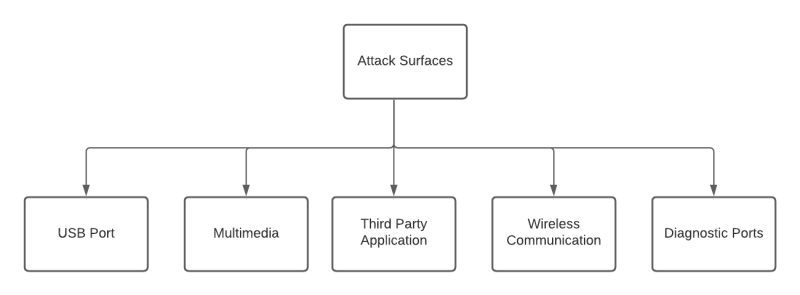
The above image shows some common attack surfaces in automotive.
USB Port : With USB attack on media playback are highly possible along
with updating firmware via USB with unauthorized code. Some of attack
vectors include following possibilities
i.Running a shell script and install malicious software
ii.Port scanning with USB to ethernet converter and detect vulnerable
networking services
iii.DMA(Direct Memory Access) attack against USB by plugging
maliciously preprogrammed hotplug device like Digispark ATTiny USB
Multimedia: The sources for multimedia playback are CD,
USB,Bluetooth,Aux,UPNP etc.
Malformed media files can be used to exploit media engine services which
can give access to system Also intentionally coded multimedia files via
CD/USB can become a trojan, thus when played may alter firmware or give
access to an attacker to vulnerability.
Third Party Applications: The third party applications are added in the
ecosystem of automotive vehicles. These apps can either be installed
directly on IVI or installed via a smartphone that connects to IVI
remotely. The vulnerability in such applications can undergo MITM
attacks between application and server as the majority of such apps are
connected to the cloud.
Wireless Communication: The WiFi and BLE communication finds the
following vulnerabilities .The wifi used in automotive as DSRC
(Dedicated Short Range Communication) with protocol such as Invehicle
Internet and Vehicle 2 Everything (V2X)
a.Vulnerability with WiFI
i. Packet sniffing, Jamming and MITM
ii. Common weakness such as open Wifi and weak encryption
iii. Open port scan if Wi-Fi hotspot available in the vehicle
BLE on other hand used in infotainment systems communicates with ECU and
is processed by AIPM (Accessory Protocol Interface Module). It is
responsible for calls, messages and notifications. Following are attack
scenarios for BLE in automotive context
i. DoS by disabling the bluetooth connectivity with driver smartphone
ii. Intercept calls or messages with MITM attack
iii. RCE (Remote Code Execution) is possible
iv. Unpaired and paired attack when device was previously paired.
Diagnostic Ports : The OnBoard Diagnostic II (OBD II) port provides
complete access to CAN bus with codes for different operations of
peripherals. It can result in replay attacks.
Other Attack Scenarios
As shown in above picture let us discuss different attack scenarios in automotive domain.
PATS : Passive Anti Theft system (PATS) is one of the bear minimum
features the car manufacturers provide. The chip in the ignition key
communicates with the transponder over a steering column via unique
code. When transponder response matches the key code results in
successful ignition. The RF communication happens at 434 MHz, thus with
RF hacking the code can be updated by an attacker. This in turn denies
the ignition start by original key or unauthorized start by an attacker.
TPMS : Tyre Pressure Monitoring System (TPMS) is an independent module
to monitor the pressure of tyres on a continuous basis. It gets
controlled by an independent ECU.Whenever the pressure in the tyre falls
below the safety level, there’s a radio signal communication
between the ECU and the tyre pressure monitoring module. Inside, each
tyre receiving sensor is wired into this smart junction box of the
car.The Smart Junction box can emit very low power, in frequency range
of 15 MHz to 434 MHz. The modulation used is amplitude shift keying
(ASK) or frequency shift keying (FSK). The attack scenario can be where
an attacker gets access to ECU and displays the incorrect readings of
low pressure.
RKE : Remote Keyless Entry (RKE) has a key fob that communicates with
ECU. Communication range is between 5-20 m approximately. The key fob is
responsible for lock/unlock, ignition,power windows control and alarm
system. It transmits encrypted radio signals ,the smart key ECU decrypts
the data which is then matched with stored data sequence and gets
successful authentication. Finally key fob gets connected to CAN and LIN
bus. Following are some attack scenarios:
i. DoS attack by disabling the key FOB by jamming signal and learning
the sequence of data
ii. Transmitted frequency received and cloned using Software Defined
Radio (SDR) gadgets available in the market. Majority vehicles use
frequency of 433 MHz or 315 MHZ with Phase Shift Keying (PSK)
modulation.
iii. The vehicle can be locked or unlocked by an attacker with RCE
Telematics : Telematics systems in autonomous vehicles are navigation
systems such as GPS and GALILEO. The weather info and locations are
being updated via these systems. The RF attacks on modulation scheme of
baseband radio of module as well as GPS spoofing results in wrong
navigation and false weather info.
File System and Services: The NAND flash is being used in automotive to
store and fetch data at high speed. Initial Program Loader (IPL) is a
bootloader which is executed as soon as ignition turned on.Embedded
Transaction File System (ETFS) is R/W directory structure and stores
data in structured format.
Different services such as NATP, Monitor service, 3Proxy,HMIGATEWAY,
WICOME,SAS service are being used in car.
The successful attacks on above mentioned file systems and services can
alter the operation of ECU.
Summary
To summarize, in this blog common attack surfaces in automotive have
been considered. The IVI system has attack surfaces viz. multimedia, USB
ports, diagnostics,third party applications and wireless communication.
We have discussed possible attacks on such interfaces. Other than that
some of other attack scenarios related to theft such as PATS and RKE
have been discussed. The RF attacks viz. TPMS and Telematics that are
low and high risk respectively have been briefed.
References
1.Amara Dinesh Kumar, Koti Naga Renu Chebrolu, Vinayakumar R, Soman KP
“ A Brief Survey on Autonomous Vehicle Possible Attacks,Exploits and
Vulnerabilities” Oct 2018,
arXiv:1810.04144v1
2.Lin tong,Cheng Luhai, “ Common Attacks Against Car Infotainment
Systems ”,Automotive Linux Summit July 2019.
https://events19.linuxfoundation.org/wp-content/uploads/2018/07/ALS19-Common-Attacks-Against-Car-Infotainment-Systems.pdf
3.UCSD and University of Washington “Automotive Attack Surfaces”
https://adambates.org/courses/cs598-fa16/slides/cs598-24-slides-auto-attack-surfaces.pdf
4.Automotive Cyber Security: A Crash Course on Protecting Cars Against
Hackers
https://www.thesslstore.com/blog/automotive-cyber-security-a-crash-course-on-protecting-cars-against-hackers/
5.A. Chattopadhya, K.Lam , “Security of autonomous vehicle as a
cyber-physical system”, 2017 7th International Symposium on Embedded
Computing and System Design
6.https://www.evelta.com/blog/introduction-to-automotive-electronics/
About Payatu
Payatu is a research-powered cybersecurity service and training organization specialized in IoT, embedded, mobile, cloud, infrastructure security, and advanced security training. We offer a full IoT/IIoTT ecosystem security assessment, including hardware, firmware, middleware, and application interfaces. If you are looking for security testing services then let’s talk, share your requirements: https://payatu.com/#getstarted Payatu is at the front line of IoT security research, with a great team, and in house tools like expliot.io. In the last 8+ years, Payatu has performed, security assessment of 100+ IoT/IIoT product ecosystems and we understand the IoT ecosystem inside out. Get in touch with us. Click on the get started button below.