Introduction:
With the advent of IoT, everything is getting connected to the internet. Bluetooth is one such protocol which is used to connect devices to the internet as the most mobile device has Bluetooth Capability, you can check this blog on how to reverse a Bluetooth communication. There are devices called Bluetooth beacons which are used to track devices which are in close proximity, companies have started connecting these beacons to the internet with geolocation and this is one such example.
Table of Contents
ToggleThis is a case of my findings on a Smart Bluetooth Beacon from Sensegiz
The testing was done on their Android Mobile Application.
For User's privacy, the IP/End-Point is not disclosed. It will be replaced by xxx.
Findings 1: Directory indexing
It was identified on analysing the endpoint “xxx.xxxxxx.com/smspush”. The files in the location can be read by anyone and it leads to leakage of information like pem files, user image and device image of all the users
Steps:
- Open your browser and point to “http://xxx.xxxxxxxx.com/smspush”
- Traverse to /mobileapp/users/images/ to find all the user image and mobileapp/findapp/images/device_images/ points to device image.
Finding 2: User Database Download
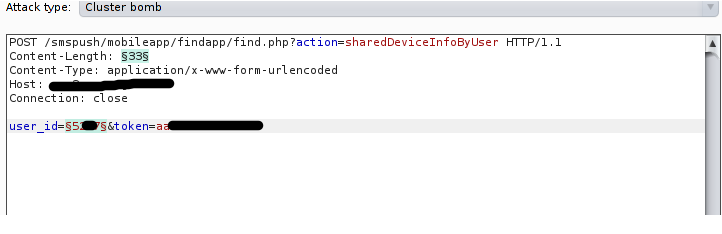
From the API call endpoint is being identified by intercepting the android app. Since the token doesn’t have any expiry time attacker can brute force the user id to get device user information like name, address and GPS location
Steps:
- Open the app and log in to your account
- Intercept the request in burp suite for user_id
- Add intruder in it and select the user_id field and brute-force the field
- Which returns information about their devices like GPS location, Device address and other sensitive information.
Finding 3: No HTTPS for communicating with the mobile app/server.
The connection from the mobile app and the server is using HTTP and it is prone to sniffing and other trivial attacks
An attacker can reverse engineer the communication to exploit the server.
Steps:
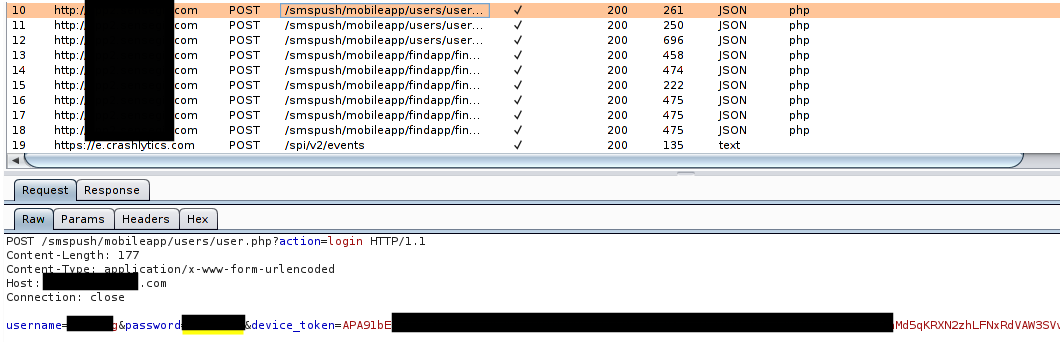
- Connect the access point to the proxy of your burp suite
- Now login to the app and look at the proxy history
You can see the sensitive information like password and other requests were sent in plain text.
Responsible Disclosure:
Reported: May 1, 2018
Vendor Response: May 13, 2018
Reminder for public disclosure: June 19, 2018
Disclosure: Nov 27, 2018
Conclusion
This analysis is based on the technologies and known threats as of the date of this report. The vendor has not fixed the bugs and they are vulnerable.
With fast-moving startup culture, vendors need to look into security and not compromise on user’s privacy and safety.