I have been working with Bluetooth for quite some time. I chose to reverse engineer a smart device to prove how crazy is the security standard being implemented in these smart devices.
In this post, I will be showing you how I reverse engineered a Bluetooth based (Smart) Massager and how I could exploit it to make it lethal.
Now how is a massager lethal?
Massager works on a principle called as TENS — transcutaneous electrical nerve stimulation. Our entire nervous system works based on neural impulse, which is electric signals. Sense of pinch to the sense of orgasm is an electrical impulse which is going to secrete different hormones in your brain and you feel pain or pleasure.
These TENS devices are attached to a region of our body using gel electrodes which need to be massaged and it starts sending small electric signals with a specific frequency which cancels the pain signal that’s going to reach your brain. These are mostly in the range of 50 to 300V at 10 to 500mA with 1 to 250HZ.
Problem is if any of these parameters are manipulated it could result in a painful experience like sudden muscle reflex, skin burn or even damage to nerves.
Before I dig into the how of it. let me first give you a short introduction on Bluetooth LE/4.0+. Nothing deep. Detailed information is already available here
Bluetooth LE/4.0+ is completely different than your Bluetooth Classic. As the name says, it has a very low power consumption of around 15–20 ma at transmission, Which makes it easier to build battery-powered applications to last longer like the smart watch, beacons and this smart massager.
Bluetooth works like server-client. where the client is called as “central” which are your mobile phones/laptop and server is called as “peripheral” which are your end devices like wearable, beacon and sensor networks.
Every device will have one or more “services” in it. Based on their functionality they have different services, for example, Smartwatch will have one service for device information, one for heart rate information and other for the firmware update.
Inside these services, you will see a lot of parameters called “characteristics”. These are basically the place where your application and the device sends and receives the data, This is entire process is handled by generic attribute profile in the Bluetooth LE stack.

Next question will be is there any security mechanism if you want to access these data??
Yes. Bluetooth does offer an option to secure your communication. It is a three-step process.
1. Connecting — The central device just connects to the device and can access all the data in the GATT.
2. Pairing — The central device needs to pair using any I/O so any new device that tries to connect to it needs physical access. This is where all the data is being encrypted with AES when transmitted into the thin air which also transmits the key in it.
3. Bonding — This allows the device to connect to the already paired device using the pre-exchanged key which happened during pairing.
The problem with pairing is that for these devices like a smart bulb or smart beacon, it becomes hard to keep a keypad or display to pair to it so the device just works on the connection without any pairing. it becomes easier for anyone to connect to it and gain access to the GATT.
Now let’s talk about how I reverse engineered the Bluetooth massager
I want to open the device and show you possible attack vectors on the hardware but i will keep it for the next blog since JTAG is located in the device.
I downloaded the official mobile application and tried to understand the inputs and outputs in the UI aka functionality.
So the application allows me to change
1. Mode of massage.
2. Intensity of the massage.
3. Timer to stop the massage.
4. View Battery level and scan for devices.
Next step is to check if the device has any kind of pairing or any security mechanism.
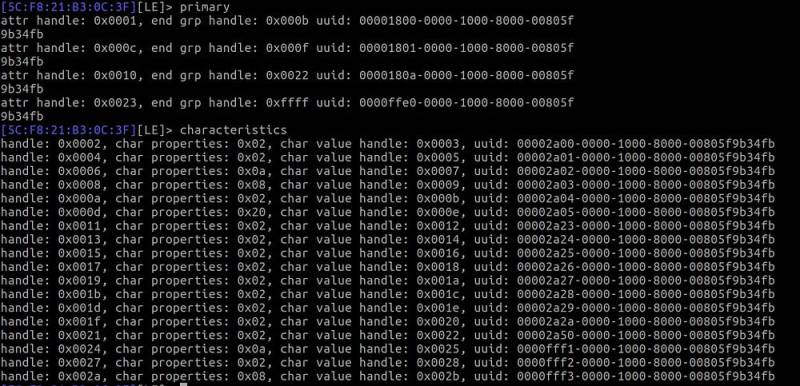
I used an android application called as “nrf connect” which is a GATT explorer that can connect to the device and lists all the services and characteristics.
I turned my massager ON and tried connecting with the massager.
Tada! It got connected. Now I can read and receive data on its characteristics.


Now I know the data is not encrypted and all transaction in GATT is in plain text or at least I believe so. Still, there is a possibility that the data could be encrypted. Still, it was a sign of relief.
This can be also be done in your laptop’s Bluetooth by using GATTool.
So we now know how to access the GATT services and how to read and write to them. Now the question is how do you know what to write to these characteristics to control the device without the mobile application
So there is this one tedious method which i use to do.
Android mobiles have an option called as HCISNOOP, which dumped all the Bluetooth communication from and to the mobile phone into a file. It can be enabled inside your developer option.
I did a considerable amount of operations from the application and the device so data can be logged.
I opened the log file in Wireshark and filtered for only GATT protocol(since my phone is a central and can perform lot of other BT protocols)
Viola! I found few GATT write and read request on handle “0x0025“ which is “0000fff1–0000–1000–8000–00805f9b34fb”.
Now the problem is how do I know which data is used for which operation. It will take some time to analyze and understand the data format and I am lazy to do that.
Since I am lazy, I use another tool which is a MiTM(Man in the middle) Bluetooth framework called as GATTacker by Sławomir Jasek(securing.pl).
Trust me it’s an amazing tool.
You can check their GIT repo on how to install it.(you do need two machines or one VM +host with 2 BT4.0 dongles).
GATTacker typically converts your laptop as a Bluetooth proxy so the device connects to one dongle and the mobile application connects to another dongle which emulates the device and we can capture the data actively.
Active analysis! That’s why I love it.
The first step is to do a scan, which scans and copies the advertisement data into a file.
Next step is to scan the device and clones all the services and characteristics in a file.
Third step is to start advertising the Advertisement and services files.
Once the service is running. the GATTacker connects to the device and you can use the app to connect to the Device which is emulated by GATTacker.
You can see in the log that the client is connected.
Now perform various operations like setting it to different modes, intensity and time and analyze which type of data is being transmitted.
So by analyzing the data, we notice for every new connection a chunk of data is being transmitted and then followed by another packet and these don’t change for different connections so it is some kind of initializing data.
For every second the mobile application send a data and the device responds, this looks like data exchange to synchronize the activity.
When I performed different operation, I got the specific packets which could be used to control the operation of the device. Now let’s compare the data between different settings.
12 34 56 78 90
a1 04 01 01 0a — Mode 1 with intensity 1 and 10 minutes
a1 04 07 02 0a — Mode 7 with intensity 2 and 10 minutes
a1 04 01 05 04 — Mode 1 with intensity 5 and 4 minutes
1234 looks like the header in hex
56 is the mode in hex
78 is the intensity in hex
90 is the time in hex
These data are written to “fff1“ whose handle value is “0x0025“ as found in Wireshark and GATTool.
Now based on this analysis we could reverse engineer the operation and control the device without the need for the mobile application.
We now know how to access the GATT and reverse engineer the data. Now let’s craft an exploit around it.
pyGATT is a python wrapper around GATT to write scripts so you can automate these communications.
All codes are available in this GIT Repo
Let’s see what’s in the code.
1. Imports all the bells and whistles aka libraries and starting Bluetooth.

2. Connecting to the device using MAC address
3. Now write data to a specific handle with the data which we RE’d
4. Close the Bluetooth connection
Now testing the script.
I don’t like to get zapped. I could hear those heavy voltage buzzing noise from my device as a confirmation that my script worked.
if anyone has tried it in their body please do share your experience.
Unless you’re this guy

I actually wanted to see if I can play a music by triggering the device, but sadly the frequency and the width of the pulse is predefined in the firmware for different modes and not controlled in GATT. I still tried. Check the GIT code if you want to zap yourself with some tone.
Happy Hacking!
By Arun Magesh
The author is a security researcher at Payatu Technologies. You can connect with Arun on Twitter or LinkedIn.