As penetration testers/security researchers, we often encounter firewalls configured with rules that make it difficult to discover and test open ports. In this blog, we will discuss and demonstrate the concept of “Source Port Manipulation” using nmap, a method that can be used to evade misconfigured firewall rules. We will also go beyond successful firewall evasion and see a technique that can help with testing services behind firewalls efficiently.
Table of Contents
ToggleFirewalls and Misconfiguration
A firewall is a device used to monitor incoming and outgoing traffic in a network based on certain defined rules. It is a barrier between a private internal network and the public internet. The most basic job of a firewall is to allow essential traffic and block threats. A lot of hardware firewalls are available in the market today, and Cisco, Fortinet, and Palo Alto, would be good examples if we were to name a few.
However, a firewall does not “magically” detect and block harmful traffic. It needs certain rules to follow based on which it manipulates traffic, and these rules are written by humans. Which means mistakes are possible.
One such mistake is allowing ‘ALL’ external traffic from essential ports like 21 (FTP), 53 (DNS), 80 (HTTP), 443 (HTTP), 8080 (alternative HTTP service), etc. This is done to allow users inside the network to access external resources. That sounds necessary at first, but the emphasis is on “ALL” traffic being allowed.

A Misconfigured Firewall
A correct firewall configuration would be to only allow RELATED and ESTABLISHED external traffic, meaning, to only allow external traffic in if the connection was initiated from inside the network. Such misconfigurations can be exploited by using a technique called “Source Port Manipulation”.
What is Source Port Manipulation
Source port manipulation refers to manipulating actual port numbers with a different number to evade IDS/firewall. This is useful when the firewall is configured to allow traffic from ports like HTTP, DNS, FTP, etc.
As discussed earlier, the firewall is misconfigured and thus allows external traffic from well-known ports, including externally initiated traffic. We can use this advantage and potentially exploit exposed internal services because of this flaw. Look at the below image of a Nmap scan. It says that port 3306 (MySQL) is closed.
$ sudo nmap -p 3306 <target-ip-address>

MySQL port returns closed when scanned from random port
Now, let’s use nmap to manipulate our source port and throw all traffic at our target via port 80:
$ nmap -p 3306 -g 80 <target-ip-address>

MySQL port returns open when scanned from port 80
We see that the firewall allows traffic through port 80. The below screenshots explain the same concept by using Netcat:
# Connection refused
$ nc -nv <target-ip-address> <target-port>
# Connection allowed
$ nc -nv -p 80<target-ip-address> <target-port>
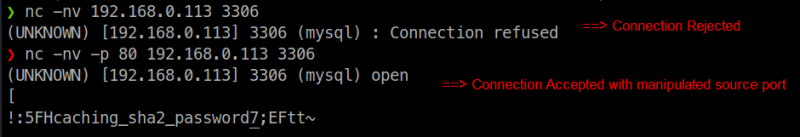
Source port manipulation with netcat
Going Beyond Source Port Manipulation
Alright, there is a misconfiguration with the firewall, and you can manipulate source ports to connect to exposed internal services. But now what? You cannot test services like MySQL by using netcat. What if the service is web-based? You would probably like to use your browser for services like Jenkins.
The answer is quite simple. We will use a firewall to defeat the firewall.

Thanos used stones, I will use Iptables
We simply create an iptables rule that will translate our source port to 80, or any other allowed port when post-routing packets to the target server. This causes the target firewall to allow the traffic, and thus we can now connect to the exposed service.
$ sudo iptables -t nat -A POSTROUTING -d <target-ip-address>
-p tcp –destination-port <target-port> -j SNAT
–to :<manipulation-port>

After you are done testing, remove the rule with the below command to stop source port manipulation:
$ sudo iptables -t nat -D POSTROUTING -d <target-ip-address>
-p tcp –destination-port <target-port> -j SNAT
–to :<manipulation-port>
Fixing Issues
This misconfiguration can be easily fixed by allowing only RELATED and ESTABLISHED external traffic through the firewall. Below is the iptables equivalent example for the same:
$ sudo iptables -A INPUT -p <protocol-tcp/udp>
–dport <port-to-allow> -m state
–state RELATED, ESTABLISHED -j ACCEPT
To conclude, firewalls are often configured to allow traffic to and from certain resources. If this configuration is not configured, then it can be exploited. Source port manipulation is one way of achieving this. Using this technique, we spoof our source port, making the firewall think the traffic was generated by a resource that must be allowed through, thus bypassing the firewall completely.



