Introduction:
This is my another case of a vulnerable IoT device. In my previous blogs, we talked about vulnerabilities there was found in Smart lock and beacons. This one is a fun device, which is made for kids to learn to code and play with it. I don’t have access to the device, so I just checked on the mobile app and found series of vulnerability.
Table of Contents
ToggleThese are my findings on a Connected smart toy – MyMiko by Emotix from their Android app.
Findings 1: Hard Coded information in the android app
It was identified on extracting the android app. several hard-coded information is present. These hard-coded information involves API calls, Web Endpoints and other information which could pose a threat.
- Download the APK from the Google Play Store
- Extract the apk file. Search all the files for strings ‘http’ using grep -iRn ‘http’ and the API base URL is identified at /xxx/xxx/miko.properties.
- By accessing the BASE_URL. We get a console for the API calls.
Findings 2: User Database Download
From the API call endpoint gives a interface for all type of API keys that is performed in the app and the server.
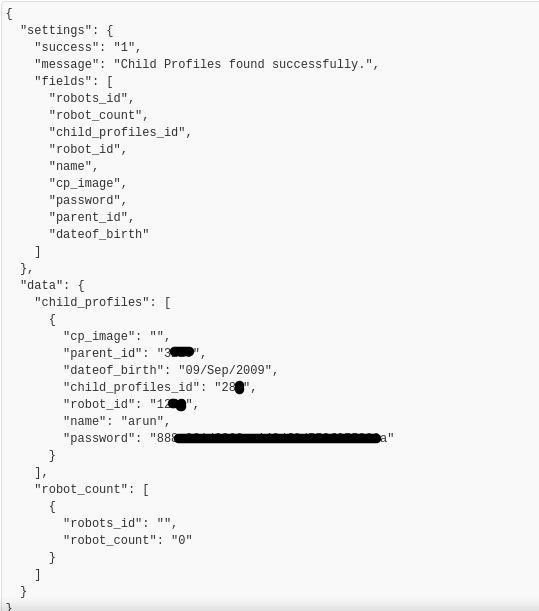
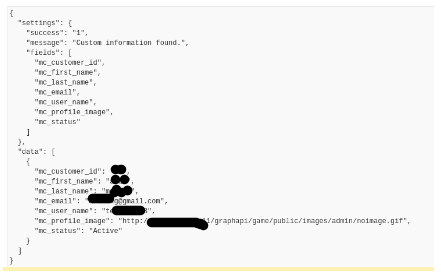
Since there is no authorisation for the API calls, Attacker can brute-force the parent id to get user information like name, phone number and email address.
Below screenshot shows the API call for parent id 3xxx
Steps:
- Access(IP removed) http://x.x.x.x/graphapi/game/WS/
- Intercept the request in burp suite for parentid
- Add intruder in it and select the parentid field and bruteforce the field
4. Now save all the response and the entire database is downloaded.
5. Similarly, ChildID, DoB, Customer information and hashed password can be also be extracted by using iParentId and CustomerID.
Findings 3: Insufficient Password retry attempt.
The Forget Password API call sends a new 6 numerical password to the user’s email address and there is no maximum retries in the mobile application and it can be brute forced easily
An attacker can brute-force the new password and gain access to the user account.
Steps:
- Access the API call for reset function and perform a reset operation
- The six numerical password sent to the Email address
- Use the Parent Login API call to login to the account and use burp suite to intercept it.
- Now use burp-suite intruder to brute force the login from 000000 to 999999
- Now save the log and find the successful response and log in using the credential and take over the account
Responsible Disclosure:
Reported: Jan 22 2018
Reminder: Apr 30, 2018
Extension of 1 more month: May 4, 2018
Reminder for public disclosure: July 17, 2018
Public Disclosure: Nov 30, 2018
Conclusion
This analysis is based on the technologies and known threats as of the date of this report. Vendor has fixed few bugs and few are still vulnerable.
Is it too early to expect secure product from startups which doesn’t compromise on security and privacy?