Hello Guys, In our last blog, we discussed some basic fundamentals about Android applications and their architecture. If you have not read my previous blog on Understanding Android Basics, then you can read it here. This will be a multipart blog series in which we will demonstrate the best way of Setting up your lab and an overview of vulnerabilities in Android Applications.
This blog will guide you in setting up your lab and some necessary tools you require for android penetration testing and also provide you a basic idea on Vulnerabilities in android applications to help you get some basic ideas.
Table of Contents
ToggleTOOLS REQUIRED
- Android Studio
- Mobsf
- Jadx
- Apktool
- Burpsuite Proxy
- SqLiteBrowser
- Frida
Make Sure you have installed all the tools to proceed next.
LAB SET-UP
- Require a System with Minimum of 4gb Ram.
- Genymotion Android Emulator OR Nox Player Emulator OR Android Studio Emulator.
- And if you are not using the above method, then we will be needing a physical device for Dynamic Testing.
Device Setup
We’ll be using Android Studio Emulator In the Android Penetration testing Blog Series.
Android Studio Emulator
- Download the Android Studio Download Android-Studio
- Open the Android Studio and click On AVD

- Create Virtual Device of Minimum of API LEVEL 26
Framework Installation
- We will first install Magisk Framework after this Xposed Framework.
- For Installation Of Magisk framework In Android Studio Emulator Install Magisk
- Follow all the steps that are given in the MagiskOnEmulator repo.
- Once Magisk Installed Open Magisk Manager Application -> Modules. Install Riru Module.

- Install Riru-Edxposed Module and Reboot the Emulator.
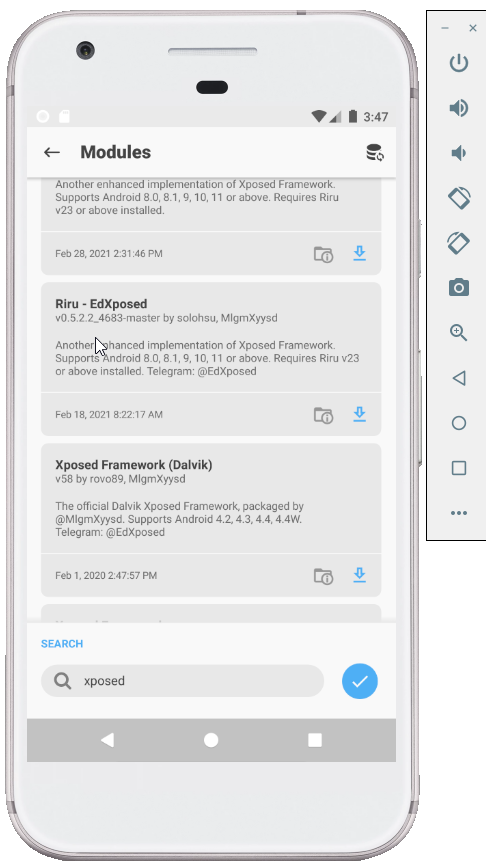
- You successfully installed Magisk And Xposed Framework.
Burp Suite Proxy Configuration
Device Configuration
- In the Burpsuite, Click on the “Proxy” tab and then click on the “Option” tab. Click on Import/export CA certificate.

- Tap on Certificate in DER Format. Proceed next.
- Save The file as extension .cer. Certificate successfully downloaded to selected Path on Your System.
- Push the Certificate in the Emulator by simply Drag and Drop. and install the certificate.
- Open Magisk and Install the Move Certificate module. This module moves all user certificates to system certificates.
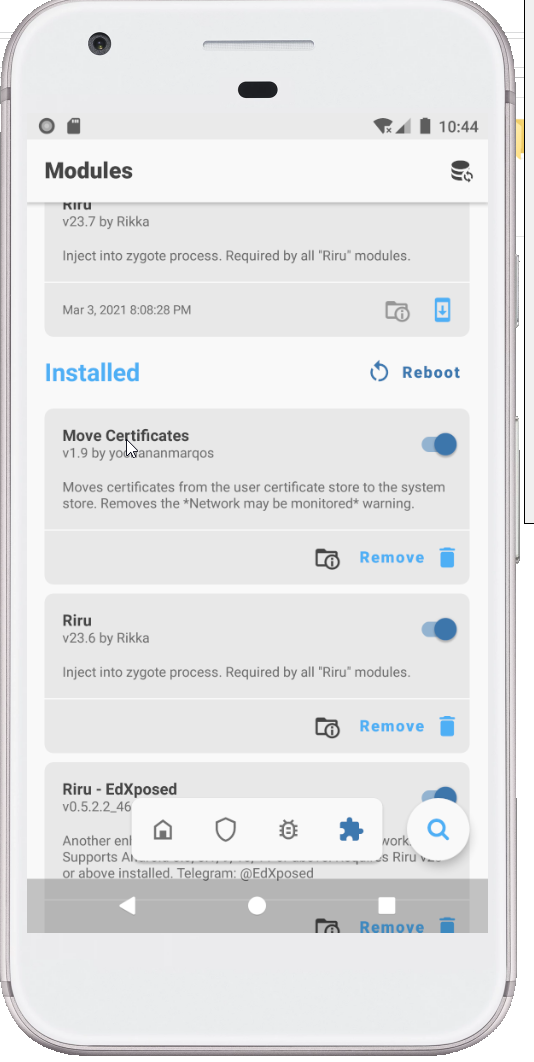
Proxy Listener Configuration
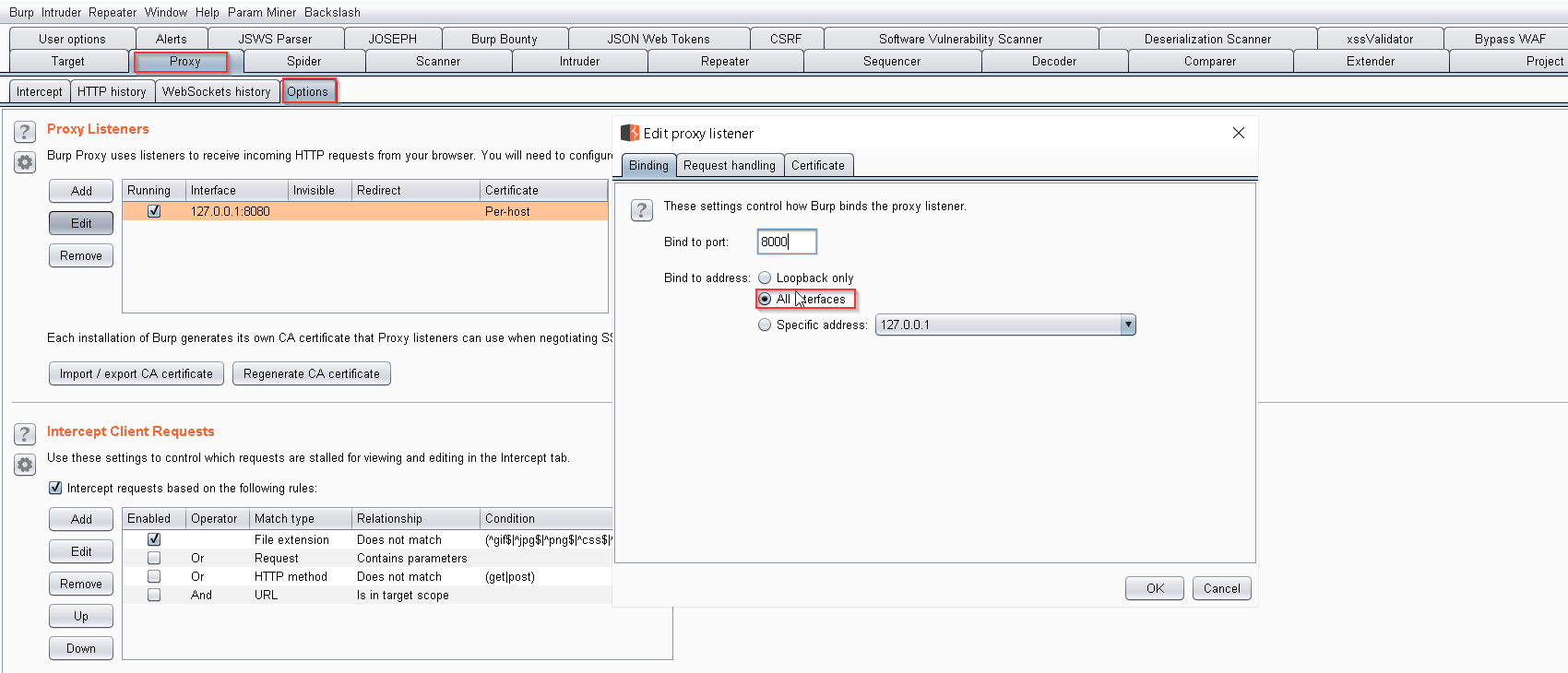
- In the Burpsuite, Click on the “Proxy” tab and then click on the “Option” tab. Under the Proxy Listeners, click on the “Edit” button
- Under the “Binding” tab, in the “Bind to port” text field enter a port number that is not currently in use. Then select the “All interfaces” radio button and click on the “OK” button
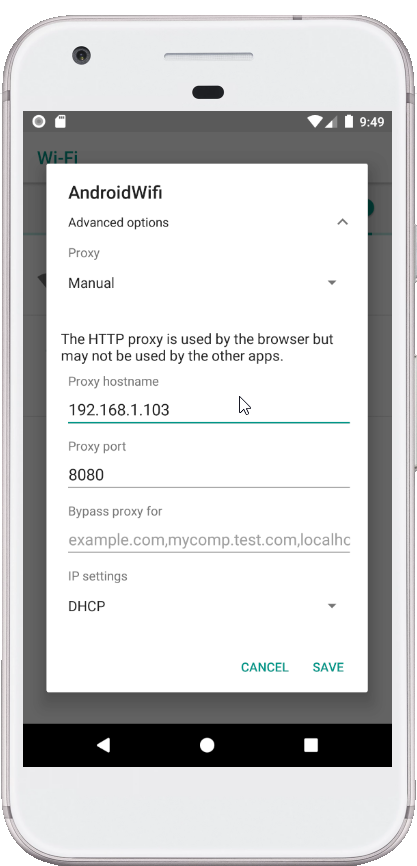
- Go to the “Wi-Fi networks” table, find your network and tap it to bring up the connection menu.
- Tap “Connect”.If you have configured a password, enter it and continue.
- Once you are connected hold down on the network button to bring up the context menu.
- Tap on Modify Network .Ensure that the “Show advanced options” box is ticked.
- Change the “Proxy settings” to “Manual” by tapping the button.
- Then enter the IP of the computer running Burp into the “Proxy hostname”.Enter the port number configured in the “Proxy Listeners” section earlier, in this example “8080”.Tap “Save”.
TOOL SETUP
We will now be setting up some tools for dynamic analysis. This blog lists down some of the tools helpful for testing Android Applications. We will setup few of the tools
- Mobile-Security-Framework – MobSF
- objection – Runtime Mobile Exploration
Mobile-Security-Framework – MobSF
- MobSF is an automated, all-in-one mobile application pentesting framework that also supports Android APK files.
- To install it you will need to download it on the Machine. The GitHub repository can be found here.
# Prequesties
Install the Requirements from -> (https://mobsf.github.io/docs/#/requirements)
# Downloading and Installing the required packages
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
cd Mobile-Security-Framework-MobSF
./setup.sh # For Linux and Mac
setup.bat # For Windows
# Running MobSF Server
./run.sh # For Linux and Mac
run.bat # For Windows
Once server is running you could navigate to http://127.0.0.1:8000 to access the MobSF GUI. Now simply drag the APK you want to analyse into the upload area and MobSF will start its job.
Frida + Objection
- Frida lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, GNU/Linux, iOS, Android, and QNX.
- Objection is a runtime mobile exploration toolkit, powered by Frida, built to help you assess the security posture of your mobile applications, without needing a jailbreak.
- To install Frida and objection on Windows we will need run the below commands
# Downloading and Installing the required packages
pip3 install frida-tools
pip3 install objection
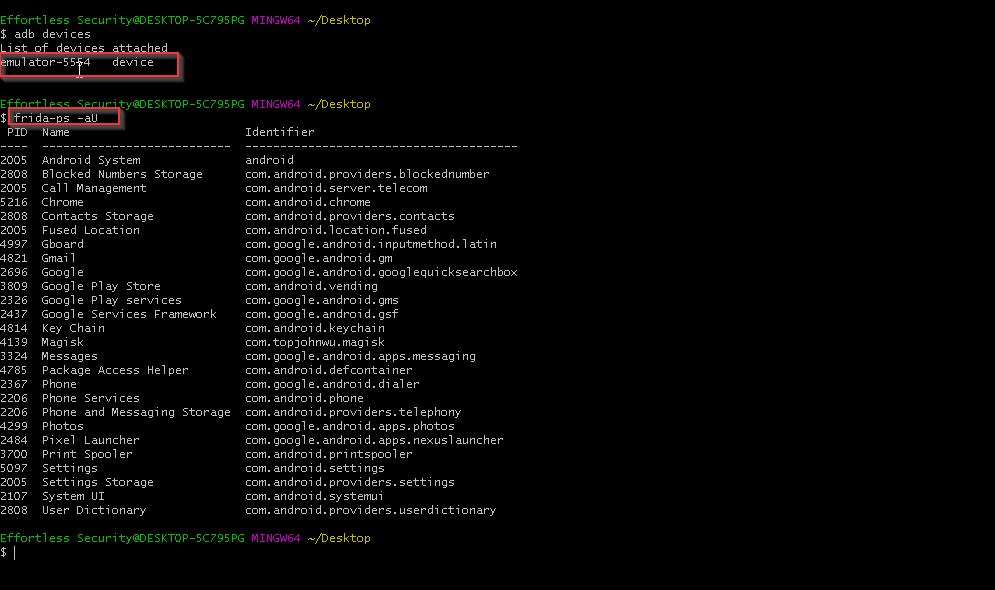
# Running Frida Client
frida-ps -U # to list the running application
objection --gadget "<package name>" explore
We also need to install a Frida server on the Android device. For the same, open Magisk Application and Install Magisk-frida Module. This Module automatically run the frida-server on boot. Restart the Device.
Suggested Read– 6 Mobile Apps to Enhance your Device Security
Vulnerability Analysis
Vulnerability analysis is typically the way toward searching for vulnerabilities in an application.Although this may be done manually, automated scanners are usually used to identify the main vulnerabilities.
There Are Two Types Of Vulnerability Analysis
- Static Analysis
- Dynamic Analysis
- Static Analysis:
Static Analysis is the analysis of an Application, which is performed without actually executing programs,. During static analysis, the mobile app’s source code is reviewed to ensure appropriate implementation of security controls. Automatic scans catch the low-hanging fruit, . Static Analysis Includes Manual Code Review, Automated Source Code Analysis. - Dynamic Analysis:
The main objective of dynamic analysis is finding security vulnerabilities in a program while it is running.
Dynamic analysis is conducted both at the platform layer and against the backend services and APIs, where the mobile app’s request and response patterns can be analyzed.
Bird Eyeview of Vulnerabilities:

About Payatu
Payatu is a Research Focused, CERT-In impaneled Cybersecurity Consulting company specializing in security assessments of IoT product ecosystem, Web application & Network with a proven track record of securing applications and infrastructure for customers across 20+ countries.
Get in touch with us. Click on the get started button below.



