Why ATOR?
The Authentication Token Obtain and Replace (ATOR) Burp plugin handles complex login sequences because it allows the user to obtain and replace authentication tokens in requests easily. This can be useful when the login process involves multiple steps or requests or when the authentication token is dynamically generated or changes frequently. The plugin can also be used to automate logging in to a website, saving time and effort when performing security testing or other tasks requiring repeated login attempts.
Note: Please be advised that the ATOR plugin is utilized for obtaining and replacing a new Authentication token with the old one. This plugin is neither considered a vulnerability scanner nor an automated scanner.
These days, automated scanning and session handling are challenging for web applications, especially given the following vectors:
- JWT
- CSRF Tokens
- APIs With authentication tokens
- Use of dual tokens (access/refresh tokens)
Features of ATOR
A straightforward and simple-to-use plugin.
- To support complex scenarios, make the plugin generic.
- Avoid repeated requests and, wherever possible, alter parameters in memory.
How the Plugin Works:
Let’s use an example to explain how the plugin works: Let’s say an access token is active for 30 seconds before it expires (a new access token has to be fetched).
Image referred from:

ATOR Working
- (0-29th min) — Genuine token. When ATOR determines that the request is authentic, it is sent to the server.
- (30th min) — Expired token. The error condition has been met, according to ATOR. The new access token (let’s say AT2) is fetched after the login sequence has finished. This authorization code is kept in memory.
- A new access token must be used between minutes 31 and 59. ATOR maintains replacing the header with AT2 until the error condition is reached because it has an access token (AT2 stored in memory). When step 2 is finished, let’s say on the 60th minute, the error condition is met.
Installation of ATOR:
- You can download it through the BApp Store ATOR (v2.1.0)

ATOR Configuration
2. It is advised that you configure Burp to accept traffic from the Flow or Logger++ extension.

ATOR Installing
How to use:
- Determine the login sequence (from the repeater or proxy) and submit it to ATOR.
- Discover the Error Pattern.
- Regex is used to retrieve the data from the answer (see sample regex values).
- Change these details on the request (use the same regex as step 3, along with the variable name).
Error Pattern in ATOR:
- The status codes 401 and 400.
- Give any text from the body content in case of a body error (Example: Access token expired).
- Header error: provide any content from the header (Example: Unauthorized).
- Use this to provide several conditions in free form Access token expired is contained in the body of the message with the status code 400 (st=400 && bd=Access token expired || hd=Unauthorized). When 400 can be thrown in several instances, this is helpful.
With samples and regex
- Use Authorization: Bearer \w* to match Authorization: Bearer HACKERSHREYAS
- Use Authentication: Bearer ([\w+_-.]*) to match Authorization: Bearer HACK-E+RSH.REYAS
A little about ATOR Screens
- Error Condition
Here, we define the error condition pattern. For example, an error like 401 will appear when a token expires. Once this error pattern has been identified, it can be added to create requests with new tokens.

Error Condition
2. Obtain Token
Here, we define the Token Extraction List location for token replacement.

Obtain Token
3. Error Condition Replacement
For the replacement area, we can define several trigger conditions and Regex patterns.


Error Condition Replacement
4. Preview
Here, we can view information about all configured conditions. We can run tests after observing all conditions.

Preview
Configure ATOR for the Payatu Sample application.
As an example, let’s walk through the Payatu Labs’ sample application.

ATOR With Sample application
This is an example POST method request to obtain profile information. When wanting to run a scanner to check for vulnerabilities would be time-consuming, we will use ATOR to avoid the token expiration problem. ATOR can generate a new token after detecting an error code condition and trying to continue the process. This particular method uses authToken to validate the application API Endpoint and expires after 5 minutes.
ATOR Settings
- Identify the login process.
In this example, we’ll use a simple one-step login to obtain each new access token.
This POST /api/v1/login API is responsible for obtaining a new token and authenticating the user in this case. So, in order to generate a new token after the expiration of the old token, we need this specific API for ATOR Obtain Token settings in the following steps.

Identify the login process.
2. Identify the Error Condition.
After successfully obtaining the token, we must now identify the error pattern in order to generate a new token. So, after logging into the application, navigate to any API using your newly created token to find out its current status. Here, we must identify the error pattern for this specific API POST /api/v1/getProfile to obtain user information using this method. I just altered the token and sent the request to generate the error condition, which resulted in a 403 error.


Identify the Error Condition
All you have to do is send these 403 requests to the ATOR Error condition tab and to generate a new token with the given error pattern, add a condition using the status code in the Trigger Condition section.

ATOR Error condition
3. Specify the pattern for replacement.
In this example, the access token is obtained from the response, and a regex pattern could also be used.

Specify the pattern for replacement
4. Modify this data on the request.
In this example, we replace the authToken in the cookie header.
Now open the Error Condition Replacement Tab. Give replacement area to the authToken Parameter.
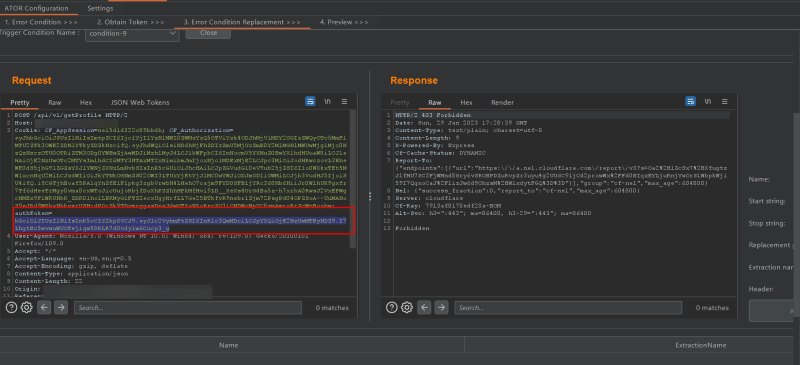
Modify this data on the request
Give replacement area to the authToken Parameter.

Modify this data on the request
5. Preview and Test Run
Now click the preview tab to check the configuration of every pattern. If everything appears good, perform the test.
Original Request POST /api/v1/getProfile with an invalid token or expired token.

Preview and Test Run
ATOR Created a new token for the API (POST /api/v1/login)
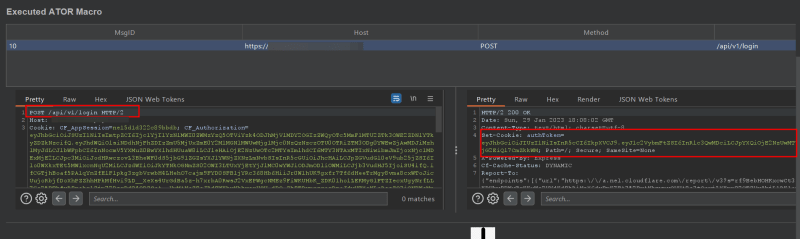
Preview and Test Run
For a replacement area that was triggered by an error condition, ATOR has replaced a new token. (POST /api/v1/getProfile )

Preview and Test Run
The ATOR restarts the login process and saves the most recent token in memory when the server returns a status code of 401. After checking the flow for it, it resends the previous request with the newly created token.

Preview and Test Run
Video Demo:
Conclusion
For demonstration purposes, we have successfully configured the ATOR for this Payatu Labs’ sample application. To avoid token expiration while running any automated scans, a simple ATOR is utilized for complicated login processes.
Acknowledgments
- Many thanks to Fruh for creating Custom Macro Extender.
- We appreciate Synopsys allowing us to open-source the plugin.
Reference:
- https://www.synopsys.com/blogs/software-security/ator-burp-plugin-login-sequences/
- https://github.com/portswigger/ator
About Payatu
Payatu is a research-powered, CERT-In empaneled cybersecurity consulting company specializing in security assessments of IoT product ecosystem, Web application & Network with a proven track record of securing applications and infrastructure for customers across 20+ countries.
Want to check the security posture of your organization? Browse through Payatu’s Service and get started with the most effective cybersecurity assessments.
Have any specific requirements in mind? Let us know about them here and someone from our team will get in touch with you.



